Virtual private servers (VPS) have become an integral solution for many businesses and individuals seeking powerful hosting for various applications because of their flexibility, scalability, affordability, and control over server resources.
However, slow performance and subpar security may negatively affect the full potential of your VPS. That’s why it’s essential to understand and implement effective port management.
Properly configuring your ports can prevent unauthorized access, minimize vulnerabilities, and ensure that your applications and services run smoothly without network-related issues.
By the end of this article, you’ll be well-equipped to maintain better control over your server’s ports and environment to maximize security and performance.
Let’s delve into the intricacies of VPS port management!
Understanding VPS port management
Ports are communication endpoints acting as gateways that enable communication between different services and applications on a server. They allow devices to send and receive data, facilitating different types of network traffic.
Imagine your VPS as a bustling city with numerous buildings and establishments. Each building represents a specific application or service running on your server, such as a website, email server, or database. Now, think of the ports as the entrances to these buildings. To ensure the smooth functioning and security of the city, you need to have a well-regulated system for managing these entrances.
Ports operate via the Internet Protocol (IP) networking model. Each IP address has a myriad of ports available, each with a unique number assigned to it, ranging from 0 to 65535, allowing for a vast range of potential communication channels.
Just as a street address ensures a package reaches the correct building, an IP address ensures data reaches the intended device, while the port number acts as the unit or apartment number.
By default, a VPS has certain ports open to allow for essential services like SSH (Secure Shell) or HTTP (Hypertext Transfer Protocol). However, leaving unnecessary ports open can pose security risks. That’s where port management comes into play.
Port management is the process of controlling which ports are open or closed on your VPS. By selectively opening the ports for the services you need and closing the unnecessary ones, you can enhance security and reduce the attack surface of your server.
But how do we know which ports are necessary and which aren’t? To answer this question, we must first explore internet protocol types and their use cases.
Different internet protocol types
Two fundamental protocols are crucial in transmitting data over the internet: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
They are both transport layer protocols residing in the fourth layer of the OSI (Open Systems Interconnection) model. They serve as the backbone of network communication, allowing devices to exchange information reliably and efficiently, but they differ in their approach and characteristics.
Transmission Control Protocol (TCP)
TCP, often referred to as a connection-oriented protocol, is designed to provide a reliable and ordered data delivery mechanism. It ensures that data packets are received by the intended destination in the correct order, without any loss or duplication.
This level of reliability is achieved by establishing a connection, known as the three-way handshake, between the sender and receiver. This confirms the readiness of both parties and sets up the necessary parameters for data transfer.
The three-way handshake allows the sender and receiver to synchronize and agree on the terms of communication. Once the connection is established, TCP breaks the data into small chunks called packets, which are then sent bidirectionally. This ensures that the packets are delivered correctly and that any lost or corrupted packets are retransmitted.
Having said that, TCP’s reliability comes at the cost of increased overhead and latency. The acknowledgment mechanism and the need for retransmission in case of packet loss or errors contribute to a more complex communication process.
Nevertheless, this complexity makes TCP suitable for applications where data integrity is of utmost importance, such as web browsing, file transfer, email communication, and any application that requires accurate data transmission.
User Datagram Protocol (UDP)
UDP operates as a connectionless protocol. It focuses on delivering data with minimal delay and provides a best-effort delivery mechanism without any reliability guarantees.
It does not establish a connection or perform a handshake before data transfer. Instead, it treats each packet as an independent entity with no inherent ordering or acknowledgment mechanism. In other words, it operates on a best-effort basis, simply forwarding data packets to their destination without actively monitoring their arrival, sacrificing TCP’s reliability and error-checking capabilities in favor of speed and efficiency.
The simplicity of UDP enables it to offer lower overhead and reduced latency, making it often favored in situations where real-time communication is essential, such as online gaming, voice and video streaming, DNS (Domain Name System) resolution, and IoT (Internet of Things) applications. In these scenarios, the priority lies in transmitting data quickly, and occasional packet loss or out-of-order delivery may be acceptable without compromising the overall user experience.
That being said, TCP and UDP rely on ports to differentiate between different services or applications running on a device. When a TCP or UDP packet arrives at a device, the destination port number in the packet header determines which application or service should receive the data.
For example, if a web browser wants to retrieve a webpage using TCP, it will send a request to the server’s IP address and specify port 80 as the destination port. Upon receiving the request, the server’s operating system knows that port 80 is associated with the HTTP service, and it will forward the request to the web server running on that port.
Having a strong grasp of TCP and UDP paves the path for effective port management, helping us decide which ports should be opened or closed to ensure the safe and seamless flow of information from one device to another.
Common port blocks and their significance
Blocks help in controlling the flow of data through specific ports. This is critical because it regulates traffic and prevents unauthorized access or malicious activities over the internet.
Internet service providers (ISPs) take this preemptive measure to safeguard against potential threats and maintain the integrity and confidentiality of any sensitive data and information transmitted. They may also restrict access to certain applications or services to comply with legal or regulatory requirements by blocking the ports they use.
For instance, they might block the ports commonly employed by peer-to-peer file-sharing applications to discourage users from using these services to illegally download copyrighted content to guarantee a fair and lawful use of their network resources.
Now, let’s take a look at some common port blocks and their significance in maintaining a secure network environment:
- Port 21 (FTP) – File Transfer Protocol (FTP) is commonly used for transferring files over a network. However, leaving this port unrestricted can expose systems to potential security risks.
- Port 22 (SSH) – Secure Shell (SSH) is widely used for secure remote administration of systems. Blocking port 22, or restricting SSH access to trusted IP addresses, adds an extra layer of protection and reduces the likelihood of unauthorized intrusions.
- Port 25 (SMTP) – The Simple Mail Transfer Protocol (SMTP) port handles email transmission. Port 25 blocking is often implemented to prevent the abuse of email servers for spamming purposes, which can help organizations curtail the potential for unauthorized mass email campaigns and reduce the risk of falling victim to email-related security threats.
- Port 80 (HTTP) – Port 80 is used for unencrypted web traffic using the Hypertext Transfer Protocol (HTTP). While it is essential for web browsing, it can be an entry point for various cyberattacks. Blocking this port will force users to access websites through encrypted connections like Hypertext Transfer Protocol Secure (HTTPS) on port 443, which enhances data privacy and security.
- Port 110 (POP3) – The Post Office Protocol version 3 (POP3) port retrieves emails from a remote server. Blocking this port helps protect against unauthorized access to email accounts and prevents potential data breaches or unauthorized retrieval of sensitive information. Instead, consider using port 995 for the Post Office Protocol 3 over SSL (POP3S).
- Port 143 (IMAP) – The Internet Message Access Protocol (IMAP) port is another protocol used for email retrieval that is best blocked. It is recommended to use SSl/TLS with IMAP to ensure the protection of email communications.
It is important to note that port blocking should be implemented judiciously, as indiscriminate blocking can hinder legitimate network activities and reduce productivity. Aim to balance security and usability, ensuring that essential ports are accessible while effectively blocking those that pose significant risks.
Opening ports on a Windows VPS firewall
There are several methods to open ports on a Windows VPS firewall that depend on your server’s configuration and the tools available. Here is a tutorial for the two most common methods:
Method 1: Using Windows Defender Firewall with Advanced Security
- Go to the Control Panel and click on System and Security.
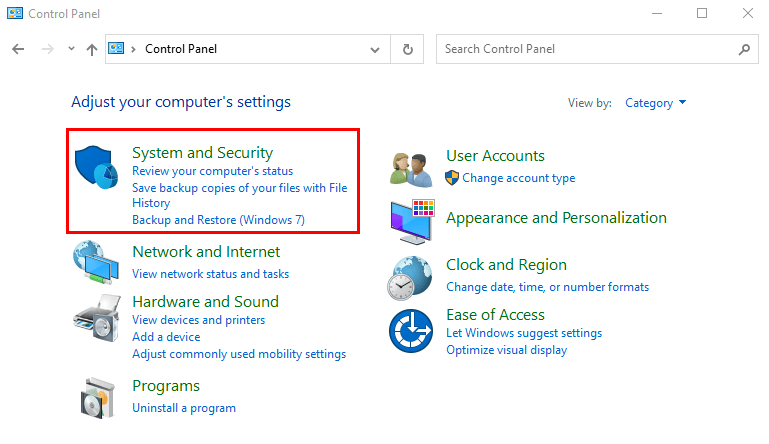
- Click on Windows Defender Firewall.
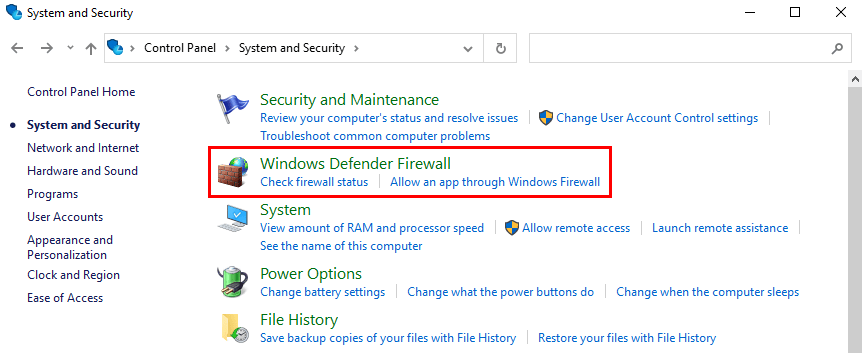
- Click on Advanced settings.
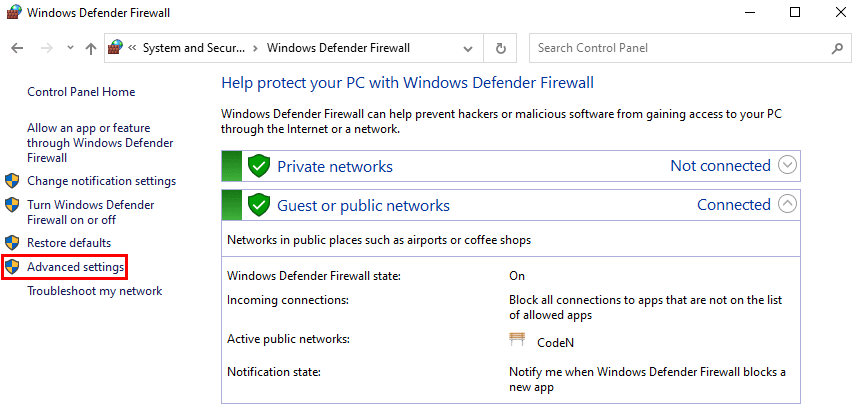
- In the left-hand pane, click on Inbound Rules.
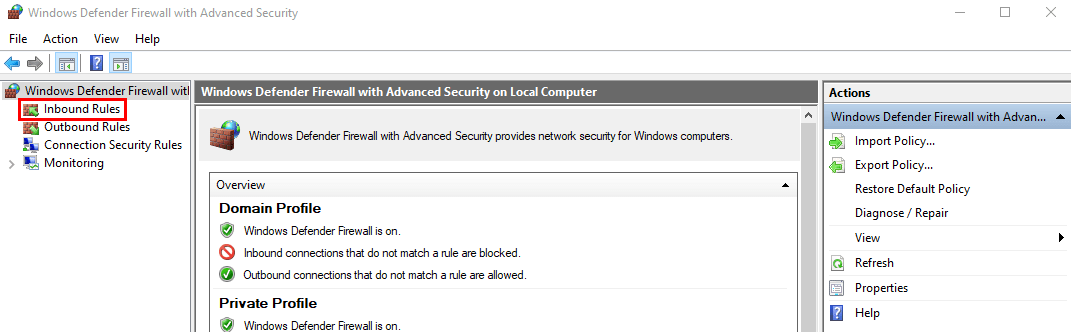
- In the right-hand pane, click on New Rule.
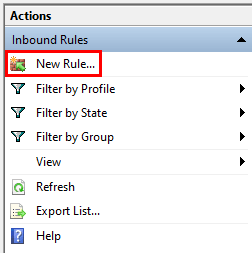
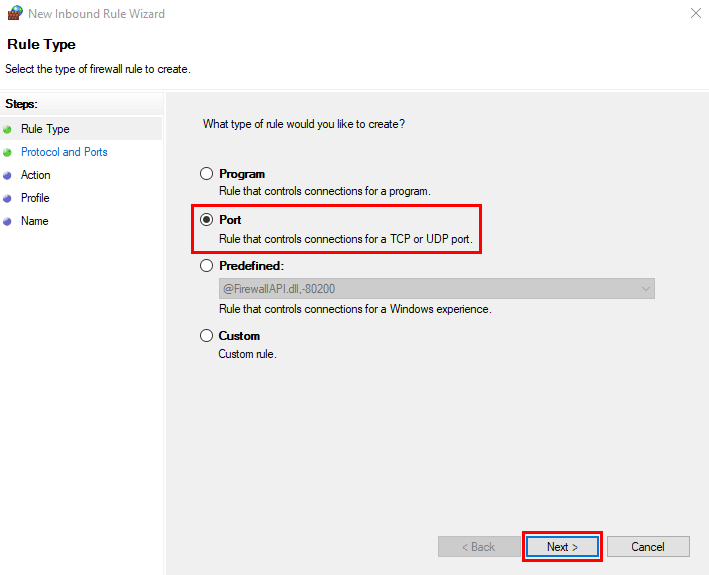
- Select Port and click on Next.
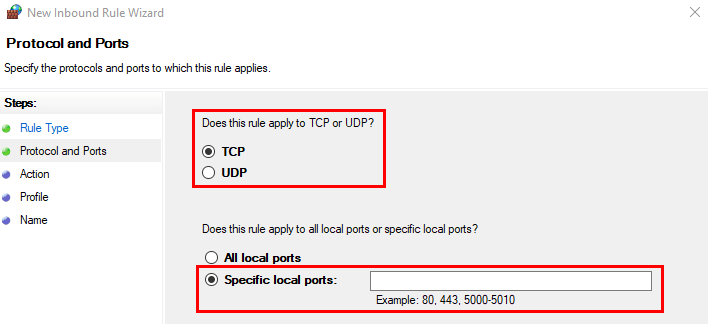
- Choose TCP or UDP as the protocol according to your requirements, and enter the port number you wish to open.
- Select Allow the connection.
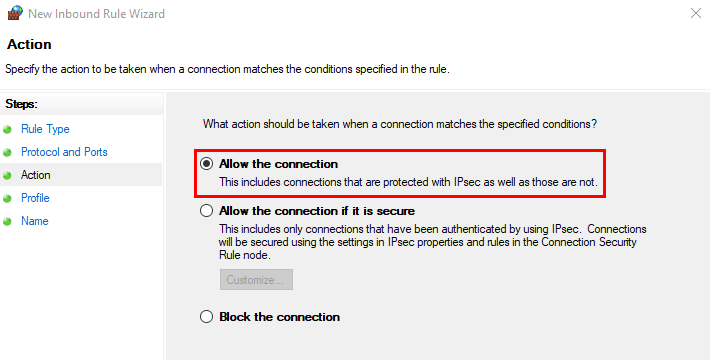
- Choose the network profiles to apply the rule (Domain, Private, or Public) according to your needs.
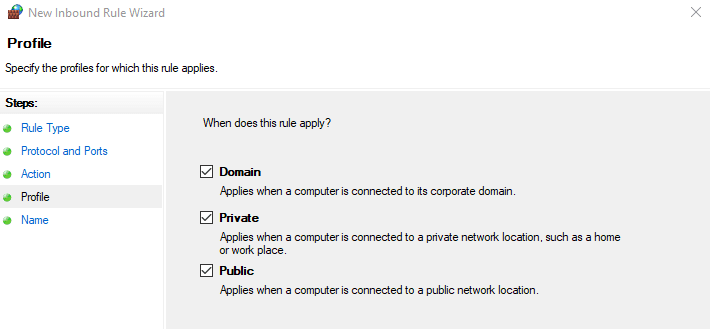
- Enter a name and description for the rule, and click Finish.
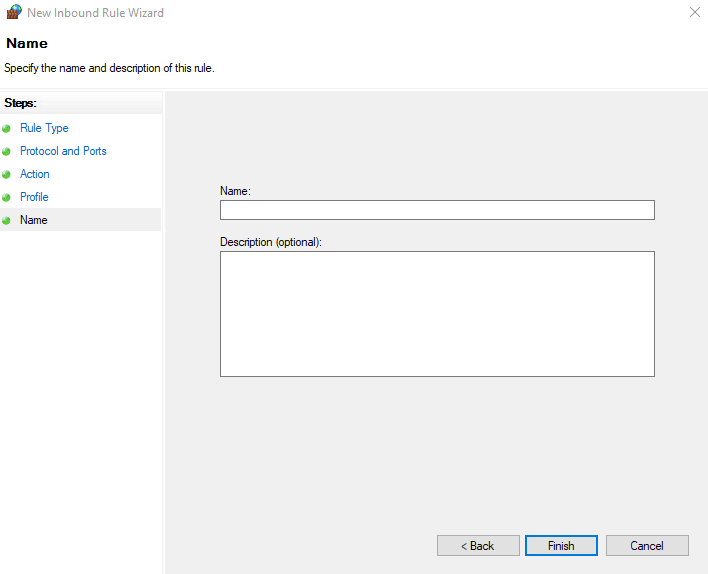
That’s it – the port that you specified should now be open.
Method 2: Using Command Prompt
- Open Command Prompt with administrative privileges.
- Run the following command to check the active connections:
- Determine the firewall profile you want to modify. The available profiles are Domain, Private, and Public. Use the following netsh command to list the available profiles and their settings:
netsh advfirewall show allprofiles- Use the following command to open a port for a specific firewall profile. Replace <PROFILE> with the desired profile name (e.g., Domain, Private, or Public) and <PORT_NUMBER> with the actual port number you want to open:
netsh advfirewall firewall add rule name="Open Port <PORT_NUMBER>" dir=in action=allow protocol=TCP localport=<PORT_NUMBER> profile=<PROFILE>For example, if you want to open port 8080 for the Private profile, your command should be as follows:
netsh advfirewall firewall add rule name="Open Port 8080" dir=in action=allow protocol=TCP localport=8080 profile=Private- Confirm that the rule has been created successfully by running the following command, replacing <PORT_NUMBER> with the port number you specified earlier:
netsh advfirewall firewall show rule name="Open Port <PORT_NUMBER>"Enhancing server security with best practices for proper port management and configuration
Your VPS serves as a cornerstone of your online presence, and any vulnerabilities can lead to potential threats and compromise your valuable data. Let’s take a look at some of the practical actions you can take to bolster your server’s security:
- Change default ports – Take, for instance, a widely employed protocol such as SSH for remote access. Altering the default SSH port, typically 22, to a non-standard port can reduce the exposure to automated attacks seeking vulnerable SSH connections.
- Limit access by IP address – Allowing access to specific ports only from trusted IP addresses can ensure that only authorized individuals or systems with predefined IP addresses can establish connections, effectively preventing malicious actors from exploiting potential vulnerabilities.
- Use secure protocols – Adopting SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols for sensitive data transmission adds another layer of protection against eavesdropping and tampering. They safeguard confidential information and mitigate the risk of interception.
- Implement port knocking – Port knocking is an additional layer of security that can be employed to obscure open ports from potential attackers. It adds an extra step for attackers to discover the open ports, making it harder to exploit vulnerabilities. This technique requires a sequence of connection attempts to predefined closed ports before a specific port opens, granting access to authorized users only.
- Regularly monitor log files and update firewall rules – A firewall acts as a protective barrier, scrutinizing network traffic and filtering out potentially harmful requests. Vigilant monitoring of logs and regularly updating firewall rules will address emerging threats or changing requirements.
- Set strong passwords – Weak passwords provide an open invitation to hackers, enabling unauthorized access. By using a combination of uppercase and lowercase letters, numbers, and special characters, you can create complex passwords that are far more resistant to brute-force attacks. Regularly change passwords and avoid reusing them on different platforms.
- Use encryption – Utilizing encryption algorithms can render intercepted data meaningless to unauthorized individuals. Implementing protocols, such as IPsec (Internet Protocol Security) or VPN (Virtual Private Network), ensure end-to-end encryption, making it exceedingly challenging for attackers to decipher sensitive information.
- Monitor and analyze log files – Regularly reviewing your log files can help you spot any suspicious activities, such as unauthorized connection attempts or unusual traffic patterns, early on so you can take proactive measures to mitigate risks.
Remember to tailor your configuration to meet your network’s requirements and employ a defense-in-depth approach. Also, avoid common mistakes that might jeopardize your hosting environment.
Avoiding common mistakes and troubleshooting issues
Not following best practices for port management may have detrimental drawbacks on your VPS, such as:
Inadequate intrusion detection and prevention systems (IDPS)
An IDPS can help detect and prevent unauthorized access attempts and suspicious activities on your VPS. Failing to implement an effective IDPS can leave you unaware of potential security breaches.
Consider installing an IDPS solution that suits your needs and configure it to alert you of any suspicious behavior or potential threats.
Lack of regular backups
Backups are essential for disaster recovery and ensuring business continuity. In the event of a security breach or data loss, having an up-to-date and reliable backup strategy that includes both on-site and off-site backups can save you from significant trouble.
Make sure that your backups are functioning correctly and can be restored if needed by regularly testing them.
Not implementing strong network security measures
Securing your VPS doesn’t stop at the server level; you also need to consider network security. Implement measures such as using secure protocols (e.g., SSH instead of FTP), enabling network encryption (SSL/TLS), and restricting access to your VPS by IP address or through a VPN.
Fixing faulty port forwarding
If you encounter issues with port forwarding on your Windows VPS, consider the following troubleshooting steps:
- Verify the port status – Ensure that the ports you need are open and available for use. You can use port scanners, such as SolarWinds Port Scanner, or command-line tools, like netstat, to verify your ports’ status.
- Examine application-specific settings – If the port issues you’re facing are specific to a particular application or service running on your VPS, investigate the application’s configuration and the exact ports that need to be open.
- Test network connectivity – Test the connectivity between your VPS and the external network to ensure there are no network-related obstacles. Ping tests (e.g., Meter), traceroute tools (e.g., KeyCDN), or even reaching out to your hosting provider’s support team can help in diagnosing any network connectivity problems.
- Check for conflicting services – In some cases, multiple services might be attempting to use the same port, resulting in conflicts. Identify if you are using two or more apps that are utilizing the same port. If a conflict exists, consider reconfiguring or stopping the conflicting service or assigning an alternative port to the applications in question.
- Seek professional assistance – If you have exhausted all troubleshooting steps and your port-related issue persists, consider contacting your VPS hosting provider’s support team. Liquid Web has one of the best around-the-clock customer support via phone calls or live chats.
Comparing VPS hosting plans and firewall software options
One vital factor that directly impacts your website’s performance is the choice of a VPS hosting provider. Selecting the right provider can significantly improve your website’s speed, security, and overall user experience.
The quality of service, reliability, and support can vary greatly from one provider to another. That’s why it’s crucial to consider the following features when choosing the right VPS hosting provider:
- Robust security measures – Ensuring the provider implements firewalls, intrusion detection systems, and regular security audits to protect your server from malicious attacks is extremely valuable.
- Optimal performance – Find a reliable provider with robust hardware resources, such as fast processors, ample RAM, and solid-state drives (SSDs) for enhanced speed and responsiveness, ensuring a smooth user experience.
- Scalability options – Choose a hosting company that allows you to easily upgrade your plan to access more server resources without disruptions as your business grows.
- Excellent customer support – Enquire if the provider has access to knowledgeable and prompt customer support for troubleshooting technical issues, optimizing performance, and addressing any concerns you may have.
Some of the best and most notable hosting providers include Liquid Web, Amazon, Digital Ocean, and Rackspace.
Among the primary factors that set Liquid Web apart from its competitors are:
- Unwavering commitment to reliability with high-availability hosting – Liquid Web has invested extensively in state-of-the-art infrastructure by having world-class data centers equipped with redundant power systems, advanced cooling mechanisms, and multiple network carriers to ensure seamless connectivity and eliminate any risk of downtime.
- Preemptive security measures – This guarantees that your online projects are safeguarded against any threat. From regular security audits and firewalls to advanced DDoS protection and malware scanning, Liquid Web takes a proactive approach to fortify its infrastructure.
- Lightning-fast response times and optimized resource allocation – This results in a seamless user experience.
- Fully customizable, scalable, and flexible solutions – You’ll be able to tailor your hosting environment precisely to your needs. Whether you are launching a small blog, an eCommerce platform, or a large-scale enterprise website, you’ll be able to seamlessly upgrade your hosting plan as your business expands, avoiding any disruptions and ensuring a smooth transition.
- Exceptional customer support with an industry-leading customer loyalty score (NPS score of 67) – Liquid Web’s dedicated team of experts is available 24/7/365, providing prompt assistance and resolving issues efficiently. Whether you have questions about server configuration, firewall settings, or general inquiries, Liquid Web’s support team is always ready to resolve your server issues. They have countless 5-star reviews to back their service.
Get started with Liquid Web’s high-performance VPS solutions
Effective port management is essential to prevent unauthorized access, protect sensitive data, and optimize network performance. Neglecting this critical aspect can leave your VPS vulnerable to security breaches, resulting in potential data loss, downtime, and a negative impact on your online presence.
Liquid Web understands the significance of VPS port management and takes comprehensive measures to ensure the utmost security and control. Their hosting solutions are designed with advanced firewall configurations, allowing for meticulous port monitoring, filtering, and access control.
Additionally, Liquid Web’s team is highly skilled and has extensive knowledge and experience in managing VPS ports. They are equipped to handle complex port configurations and offer personalized solutions tailored to your specific requirements.
Liquid Web’s proactive approach to VPS port management means potential vulnerabilities are identified and addressed swiftly, minimizing potential risks to your online assets.

